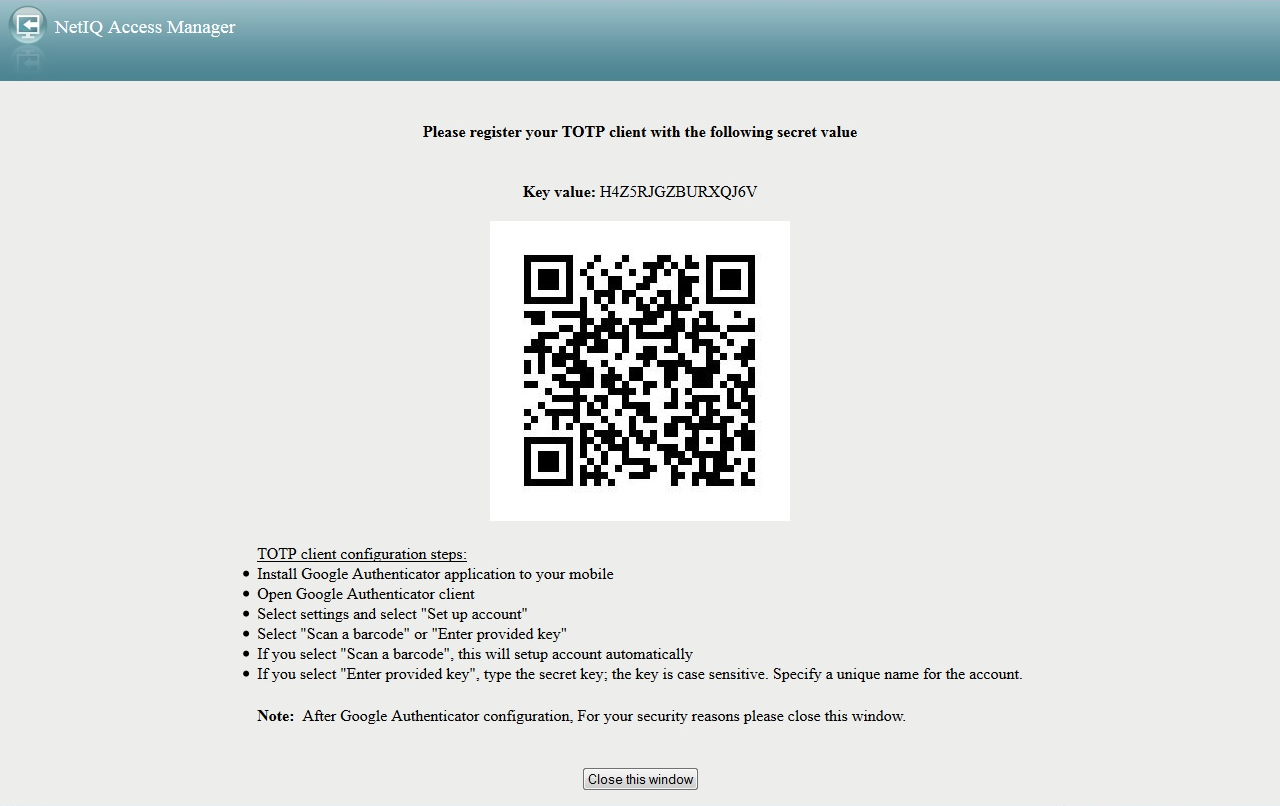
Secret Key Google Authenticator Generator
Warning: sharing your TOTP seed with third-parties breaks the very basic assumption of multi-factor authentication that the TOTP seed is secret. It will display a valid QR code, and if I scan it with my Google Authenticator app on my phone, it will begin to generate valid OTPs. Google Authenticator can issue codes for multiple accounts from the same mobile device. Each Google Account needs a different secret key. To set up additional accounts, turn on 2-Step Verification. When you switch to a new phone it can be a pain to add your accounts to Google Authenticator. (You are using two-factor authentication with important accounts, right?). This tool allows you to easily generate QR codes for your accounts as long as you have the secret key, without having to disable and re-enable 2-factor authentication on each account.
- How To Generate Secret Key For Google Authenticator
- Google Authenticator Key Code
- Secret Key Google Authenticator Generator Number
Secret keys may be encoded in QR codes as a URI with the following format:
Examples
- Apr 17, 2018 Google Authenticator is used for two-step verification based on Time-based One Time Password(TOTP) and HMAC-based One Time Password(HOTP) for authenticating users. TOTP is an algorithm that computes a one-time password from a shared secret key and the current time. HTOP is an algorithm which uses hmac algorithm to generate one-time password.
- Sep 07, 2014 Secret Key - Google Authenticator - how to recover access. Post by ozwest » Mon Dec 02, 2013 3:48 pm Hi I have changed my mobile phone and I have lost all the notes and Google Authenticator generator. Now I can not login into Joomla admin anymore as the secret key is required. How can I reset the website, so that I can access it again.
Provision a TOTP key for user alice@google.com, to use with a service provided by Example, Inc:
This Base32 encoded key 'JBSWY3DPEHPK3PXP' has the value:
Here's another example with all optional parameters supplied
Live Demo
Try Browser Authenticator Demo, source at https://git.coolaj86.com/coolaj86/browser-authenticator.js
Valid types are hotp and totp, to distinguish whether the key will be usedfor counter-based HOTP or for TOTP.
The label is used to identify which account a key is associated with. It contains an accountname, which is a URI-encoded string, optionally prefixed by an issuer string identifyingthe provider or service managing that account. This issuer prefix can be used to preventcollisions between different accounts with different providers that might be identifiedusing the same account name, e.g. the user's email address.
The issuer prefix and account name should be separated by a literal or url-encoded colon,and optional spaces may precede the account name. Neither issuer nor account name maythemselves contain a colon. Represented in ABNF according to RFC 5234:
Valid values might include Example:alice@gmail.com, Provider1:Alice%20Smith orBig%20Corporation%3A%20alice%40bigco.com.
Starting on January 1 2019, Steam has officially stopped supporting the Windows XP and Windows Vista operating systems. 
We recommend using both an issuer label prefix and an issuer parameter, described below.
Secret
REQUIRED: The secretWindows server 2016 product key generator. parameter is an arbitrary key value encoded in Base32according to RFC 3548. The padding specifiedin RFC 3548 section 2.2 is notrequired and should be omitted.
How To Generate Secret Key For Google Authenticator
Issuer
STRONGLY RECOMMENDED: The issuer parameter is a string value indicatingthe provider or service this account is associated with, URL-encoded according toRFC 3986. If the issuer parameter is absent,issuer information may be taken from the issuer prefix of the label. If both issuerparameter and issuer label prefix are present, they should be equal.
Valid values corresponding to the label prefix examples above would be: issuer=Example,issuer=Provider1, and issuer=Big%20Corporation.
Older Google Authenticator implementations ignore the issuer parameter and rely uponthe issuer label prefix to disambiguate accounts. Newer implementations will use theissuer parameter for internal disambiguation, it will not be displayed to the user.We recommend using both issuer label prefix and issuer parameter together to safelysupport both old and new Google Authenticator versions.
Algorithm
OPTIONAL: The algorithm may have the values:
- SHA1 (Default)
- SHA256
- SHA512
Currently, the algorithm parameter is ignored by the Google Authenticator implementations.
Digits
Google Authenticator Key Code
OPTIONAL: The digits parameter may have the values 6 or 8, and determines howlong of a one-time passcode to display to the user. The default is 6.
Currently, on Android and Blackberry the digits parameter is ignored by the Google Authenticator implementation.
Secret Key Google Authenticator Generator Number
Counter
REQUIRED if type is hotp: The counter parameter is required when provisioninga key for use with HOTP. It will set the initial counter value.
Period
OPTIONAL only if type is totp: The period parameter defines a period that aTOTP code will be valid for, in seconds. The default value is 30.
Currently, the period parameter is ignored by the Google Authenticator implementations.
| #!/usr/bin/env python |
| # This Source Code Form is subject to the terms of the Mozilla Public |
| # License, v. 2.0. If a copy of the MPL was not distributed with this |
| # file, You can obtain one at http://mozilla.org/MPL/2.0/. |
| # Required packages (available from pip) : pyqrcode, pypng |
| importpyqrcode |
| importbase64 |
| importos |
| importbinascii |
| #We want a secret of at least 30 hex chars for security reasons |
| SECRET_LEN=30 |
| defconvert_secret_to_base32(secret): |
| returnbase64.b32encode(base64.b16decode(secret.upper())) |
| # Google authenticator format: |
| #otpauth://totp/[KEY NAME]?secret=[KEY SECRET, BASE 32]. |
| #'Myphone nr' for example, but it can be anything, a login/uid, etc. |
| keyname='4155701111' |
| #if you want to generate a code for non-Google (ie standard OATH Hex secret): |
| #secret = binascii.b2a_hex(os.urandom(SECRET_LEN)) |
| #For Google or Google-compatible authenticators: |
| secret=convert_secret_to_base32(binascii.b2a_hex(os.urandom(SECRET_LEN))) |
| #For HOTP, just replace totp by hotp ;-) |
| qrdata='otpauth://totp/{keyname}?secret={secret}'.format(keyname=keyname, secret=secret) |
| code=pyqrcode.create(qrdata) |
| # Generate on disk |
| code.png('code.png', scale=10) |
| # Generate in memory example: |
| # import io |
| # buffer = io.BytesIO() |
| # url.png(buffer) |
| # print('<img data='{}' />'.format(buffer.getvalue(()))) |