Proxy Re Encryption Key Generation
- Ateniese, G., Fu, K., Green, M., Hohenberger, S.: Improved Proxy Re-encryption Schemes with Applications to Secure Distributed Storage. ACM Trans. Inf. Syst. Secur. 9(1), 1–30 (2006)CrossRefzbMATHGoogle Scholar
- Beimel, A.: Secure schemes for secret sharing and key distribution. PhD Thesis, Israel Institute of Technology, Technion, Haifa (1996)Google Scholar
- Bethencourt, J., Sahai, A., Waters, B.: Ciphertext-policy attribute-based encryption. In: IEEE Symposium on Security and Privacy, pp. 321–334 (2007)Google Scholar
- Blaze, M., Bleumer, G., Strauss, M.J.: Divertible Protocols and Atomic Proxy Cryptography. In: Nyberg, K. (ed.) EUROCRYPT 1998. LNCS, vol. 1403, pp. 127–144. Springer, Heidelberg (1998)CrossRefGoogle Scholar
- Boneh, D., Hamburg, M.: Generalized identity based and broadcast encryption schemes. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 455–470. Springer, Heidelberg (2008)CrossRefGoogle Scholar
- Boneh, D., Waters, B.: Conjunctive, subset, and range queries on encrypted data. In: Vadhan, S.P. (ed.) TCC 2007. LNCS, vol. 4392, pp. 535–554. Springer, Heidelberg (2007)CrossRefGoogle Scholar
- Canetti, R., Halevi, S., Katz, J.: Chosen-ciphertext security from identity-based encryption. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 207–222. Springer, Heidelberg (2004)CrossRefGoogle Scholar
- Canetti, R., Hohenberger, S.: Chosen-Ciphertext Secure Proxy Re-encryption. In: Proceedings of the 14th ACM Conference on Computer and Communications Security - ACM CCS 2007, pp. 185–194 (2007)Google Scholar
- Chow, S.S.M., Weng, J., Yang, Y., Deng, R.H.: Efficient Unidirectional Proxy Re-Encryption. In: Bernstein, D.J., Lange, T. (eds.) AFRICACRYPT 2010. LNCS, vol. 6055, pp. 316–332. Springer, Heidelberg (2010)CrossRefGoogle Scholar
- Emura, K., Miyaji, A., Omote, K.: An Identity-Based Proxy Re-Encryption Scheme with Source Hiding Property, and its Application to a Mailing-List System. In: Camenisch, J., Lambrinoudakis, C. (eds.) EuroPKI 2010. LNCS, vol. 6711, pp. 77–92. Springer, Heidelberg (2011)CrossRefGoogle Scholar
- Goyal, V., Pandey, O., Sahai, A., Waters, B.: Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM Conference on Computer and Communications Security - ACM CCS 2006, pp. 89–98 (2006)Google Scholar
- Green, M., Ateniese, G.: Identity-Based Proxy Re-encryption. In: Katz, J., Yung, M. (eds.) ACNS 2007. LNCS, vol. 4521, pp. 288–306. Springer, Heidelberg (2007)CrossRefGoogle Scholar
- Lai, J., Deng, R.H., Yang, Y., Weng, J.: Adaptable Ciphertext-Policy Attribute-Based Encryption. In: Cao, Z., Zhang, F. (eds.) Pairing 2013. LNCS, vol. 8365, pp. 199–214. Springer, Heidelberg (2014)CrossRefGoogle Scholar
- Kawai, Y., Takashima, K.: Fully-Anonymous Functional Proxy-Re-Encryption. IACR Cryptology ePrint Archive, pp. 318, 201Google Scholar
- Liang, K., Fang, L., Wong, D.S., Susilo, W.: A ciphertext-policy attribute-based proxy re-encryption with chosen-ciphertext security. IACR Cryptology ePrint Archive, 2013, 236 (2013)Google Scholar
- Liang, X., Cao, Z., Lin, H., Shao, J.: Attribute based proxy re-encryption with delegating capabilities. In: Proceedings of the 4th International Symposium on Information, Computer, and Communications Security, ASIACCS 2009, pp. 276–286. ACM (2009)Google Scholar
- Libert, B., Vergnaud, D.: Unidirectional Chosen-Ciphertext Secure Proxy Re-encryption. In: Cramer, R. (ed.) PKC 2008. LNCS, vol. 4939, pp. 360–379. Springer, Heidelberg (2008)CrossRefGoogle Scholar
- Luo, S., Hu, J., Chen, Z.: Ciphertext Policy Attribute-Based Proxy Re-encryption. In: Soriano, M., Qing, S., López, J. (eds.) ICICS 2010. LNCS, vol. 6476, pp. 401–415. Springer, Heidelberg (2010)CrossRefGoogle Scholar
- Matsuo, T.: Proxy re-encryption systems for identity-based encryption. In: Takagi, T., Okamoto, T., Okamoto, E., Okamoto, T. (eds.) Pairing 2007. LNCS, vol. 4575, pp. 247–267. Springer, Heidelberg (2007), http://dx.doi.org/10.1007/978-3-540-73489-5_13CrossRefGoogle Scholar
- Mizuno, T., Doi, H.: Hybrid proxy re-encryption scheme for attribute-based encryption. In: Bao, F., Yung, M., Lin, D., Jing, J. (eds.) Inscrypt 2009. LNCS, vol. 6151, pp. 288–302. Springer, Heidelberg (2010)CrossRefGoogle Scholar
- Ostrovsky, R., Sahai, A., Waters, B.: Attribute-based encryption with non-monotonic access structures. In: ACM CCS 2007, pp. 195–203 (2007)Google Scholar
- Pirretti, M., Traynor, P., McDaniel, P., Waters, B.: Secure attribute-based systems. In: ACM CCS 2006, pp. 99–112 (2006)Google Scholar
- Sahai, A., Waters, B.: Fuzzy identity-based encryption. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 457–473. Springer, Heidelberg (2005)CrossRefGoogle Scholar
- Arita, S.: Flexible Attribute-Based Encryption. In: Chim, T.W., Yuen, T.H. (eds.) ICICS 2012. LNCS, vol. 7618, pp. 471–478. Springer, Heidelberg (2012)CrossRefGoogle Scholar
- Shao, J., Cao, Z.: CCA-Secure Proxy Re-encryption without Pairings. In: Jarecki, S., Tsudik, G. (eds.) PKC 2009. LNCS, vol. 5443, pp. 357–376. Springer, Heidelberg (2009)CrossRefGoogle Scholar
- Shi, E., Waters, B.: Delegating capabilities in predicate encryption systems. In: Aceto, L., Damgård, I., Goldberg, L.A., Halldórsson, M.M., Ingólfsdóttir, A., Walukiewicz, I. (eds.) ICALP 2008, Part II. LNCS, vol. 5126, pp. 560–578. Springer, Heidelberg (2008)CrossRefGoogle Scholar
- Waters, B.: Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In: Catalano, D., Fazio, N., Gennaro, R., Nicolosi, A. (eds.) PKC 2011. LNCS, vol. 6571, pp. 53–70. Springer, Heidelberg (2011)CrossRefGoogle Scholar
A Proxy Re-Encryption library using Bilinear Map. It contains basic functions like encryption, decryption, re-encryption, re-decryption, sign and verify.
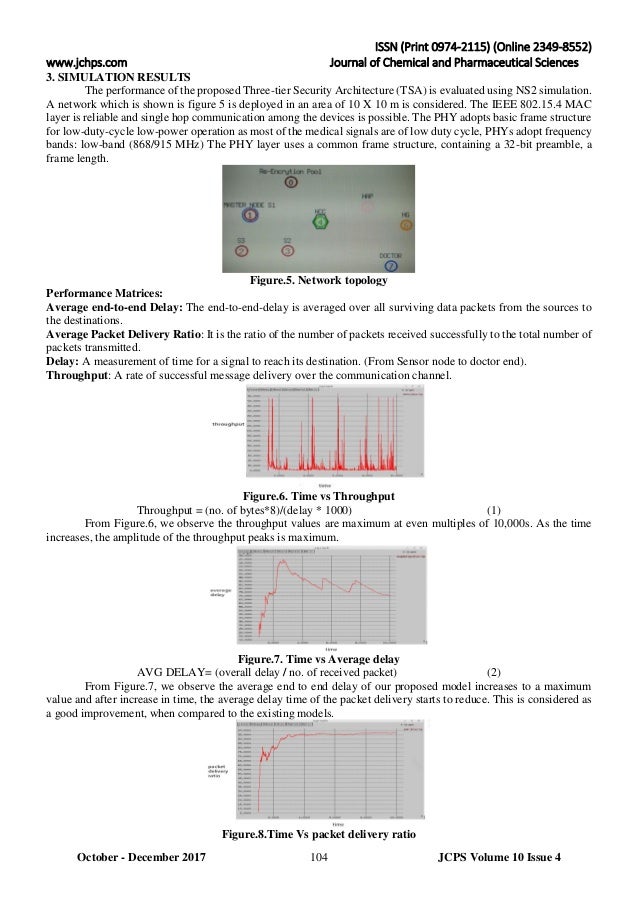
The function of proxy re-encryption with keyword search (PRES) is the combination of proxy re-encryption (PRE) and public key encryption with keyword search (PEKS). However, a PRES scheme cannot be obtained by directly combining those two schemes, since the resulting scheme is no longer proven secure in our security model. Proxy Re-Encryption provides the ability to transform a ciphertext encrypted under some key to the one under another key. This seems interesting. But, something seems strange. Suppose Alice has a key pair (ska, pka) and Bob also has a key pair (skb, pkb).
Usage
Setup
Set the generators of G1 and G2. It must pefrom at first.
Generate Random Element in Fr
PRE is supposed to encrypt symmetric key.
It's recommended to get the key from a random element in Fr and convert it to hex string instead of generating a random key and mapping it to Fr.
Generate Key Pairs
Generate key pairs of Delegator(A) and Delegatee(B).
You can get public key from existing secret key using getPkFromG1 and getPkFromG1.
Encryption & Decryption
Proxy Re Encryption Key Generation 2
A can of course encrypt and decrypt.
Generate Re-Encryption Key
A can generate reKey with A's secret key and B's public key.
Re-Encryption & Re-Decryption
Anyone can convert encrypted with reKeyinto ciphertext that can be decrypted by B.
Sign and Verify
Right now only signature by delegator is implemented, delegatee can have key pair with delegator's format (in G1) as well.
Tips
Almost every input parameters can either be hex string or Object in group. It'll automatically check the type and convert it to Object during caculation if necessary.
Algrithom
Proxy Re Encryption
Setup
$g$ and $h$ are the generators of $G_1$ and $G_2$
$Z=e(g,h)$
$e:G_1 times G_2 to G_T$
Key Generation
$sk_A in F_r$, $pk_A=g^{sk_A} in G_1$
$sk_B in F_r$, $pk_B=h^{sk_B} in G_2$
Encryption$$C_1=((pk_A)^k,mZ^k)$$
Decryption
Chevrolet Camaro Lost Car Keys Replacement Made Easy! All The Information You Need To Get a New Car Key. Cost, Type Of Keys, Where To Make a Duplicate and More. Mar 26, 2015 On May 16 Chevrolet will unveil the all-new, sixth-generation Camaro, which is why the automaker asked five designers who contributed to the styling of the Gen 5 car to talk about the Camaro’s. So you just somehow lost the keys to your 5th Gen Camaro and you are forced to replace them through the dealership. You buy the keys (roughly $160, ouch!) then realize you also have to pay the dealer separately to PROGRAM the keys as well to recognize your car. You can program your keys for FREE and save yourself around $135. All you need is about 30 minutes. These directions can also be. Hide car key on new generation camaro for sale.
$$frac{beta}{e(alpha,h)^{frac{1}{sk_A}}}=frac{me(g,h)^k}{e((pk_A)^k,h)^{frac{1}{sk_A}}}=frac{me(g,h)^k}{e((g^{sk_A})^k,h)^{frac{1}{sk_A}}}=m$$
Re-Encryption Key Generation
$$rk_{A to B}=(pk_B)^{frac{1}{sk_A}}$$
Re-Encryption
From $C_I=(alpha,beta)$
Caculate $alpha{'}=e(alpha,rk_{P to D})$
Output $C_2=(alpha ^{'},beta)$
Re-Decryption
$$frac{beta}{(alpha^{'})^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e(alpha,rk_{P to D}))^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e((pk_A)^k,(pk_B)^{frac{1}{sk_A}})^{frac{1}{sk_B}}}=frac{me(g,h)^k}{e((g^{sk_A})^k,(h^{sk_B})^{frac{1}{sk_A}})^{frac{1}{sk_B}}}=m$$
Sign
$$S=H^{sk_A}$$
Verify
$$e(g,S)=e(g,H^{sk_A})=e(g^{sk_A},H)=e(pk_A,H)$$