Generate Aes Key From Password C
Chilkat • HOME • Android™ • Classic ASP • C • C++ • C# • Mono C# • .NET Core C# • C# UWP/WinRT • DataFlex • Delphi ActiveX • Delphi DLL • Visual FoxPro • Java • Lianja • MFC • Objective-C • Perl • PHP ActiveX • PHP Extension • PowerBuilder • PowerShell • PureBasic • CkPython • Chilkat2-Python • Ruby • SQL Server • Swift 2 • Swift 3/4 • Tcl • Unicode C • Unicode C++ • Visual Basic 6.0 • VB.NET • VB.NET UWP/WinRT • VBScript • Xojo Plugin • Node.js • Excel • Go
- AES Key Generator Devon 2019-04-27T15:14:21-07:00. Below is a Base64 Encoded AES-256 key which was been generated using the secure javax KeyGenerator. This key will work perfectly with any of the AES encryption code elsewhere on my site, and probably most of yours as well. This key is secure, randomly generated, and has been generated just for you.
- Oct 16, 2019 Generate a key using openssl rand, e.g. Openssl rand 32 -out keyfile. Encrypt the key file using openssl rsautl. Encrypt the data using openssl enc, using the generated key from step 1. Package the encrypted key file with the encrypted data. The recipient will need to decrypt the key with their private key, then decrypt the data with the.
- The salt is stored where the password would be processed in order to get the correct key. Best practice is to use a PBKDF to generate a 'key encryption key' (KEK), then a full entropy random key is used to encrypt the data, and the KEK is used to encrypt that key. That way a password change does not require reencryption of all the data, just.
- If you want to manually specify the provider, just call KeyGenerator.getInstance('AES', 'providerName'). For a truly secure key, you need to be using a hardware security module (HSM) to generate and protect the key. HSM manufacturers will typically supply a JCE provider that will do all the key generation for you, using the code above.
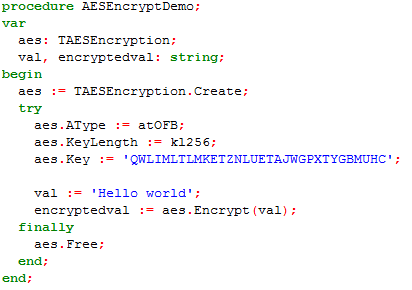
| Discusses symmetric encryption key generation techniques for block encryption algorithms such as AES, Blowfish, and Twofish, or for other algorithms such as ChaCha20.
| |||||
The cryptographic keys used for AES are usually fixed-length (for example, 128 or 256bit keys). Because humans cannot easily remember long random strings, key stretching is performed to create a long, fixed-length key from a short, variable length password. Key stretching uses a key-derivation function.

© 2000-2020 Chilkat Software, Inc. All Rights Reserved.Crysis wars cd key generator download.