Sql Server Generate Hash Key
- Sql Server Generate Hash
- Sql Server Generate Hash Key In Photoshop
- Sql Server Generate Hash Key Mac
- How To Generate Hash Key In Sql Server
Sep 26, 2018 How to use HASHBYTES function in sql server for multiple columns – Learn more on the SQLServerCentral forums. Dec 18, 2008 Creating a hash field in SQL Server is easy. The database engine has a couple of built-in functions that can be used to generate the hashed value. Two of these functions are CHECKSUM and BINARYCHECKSUM. CHECKSUM is intended to be used to build hash indexes while BINARYCHECKSUM.
Posted July 24, 2014
By Arshad Ali
Hash keys probe and residual. Say, we have a query like this: Assuming the above query uses a Hash Join and has a residual, the probe key will be col1 and the residual will be len(a.col1)=10. But while going through another example, I could see both the probe and the residual to be the same column. May 16, 2018 In SQL Server 2012, we have an enhancement in this function and now it supports SHA2256, SHA2512 algorithms that can generate 32 and 64 bytes hash codes for the respective input. Beginning with SQL Server 2016, all algorithms other than SHA2256, and SHA2512 are deprecated.
Introduction
Is using hashes for primary keys a good idea? Ask Question Asked 4 years, 7 months ago. If you pick a better hash then no human on the planet knows how to create even a single collision. Many have tried. – usr Aug 20 '15 at 18. Using a Hash or GUID as Primary Key is also bad idea because it causes Index Fragmentation and frequent Page.
In my most recent articles, I’ve talked about encryption in detail and demonstrated its usage at the entire database level with Transparent Data Encryption and at the column level with granularcell level encryption. In this article, I am going to discuss hashing in SQL Server and how it is different from encryption.
Encryption vs. Hashing
Encryption brings data into a state which cannot be interpreted by anyone who does not have access to the decryption key, password, or certificates. Though encryption does not restrict the access to the data, it ensures if data loss happens, then in that case data is useless for the person who does not have access to the decryption keypasswordcertificates. On the other hand, Hashing brings a string of characters of arbitrary size into a usually shorter fixed-length value or key that represents the original string and acts as a shortened reference to the original data. A slight change in the input string of characters produces a completely different hashed output.
To meet the demands of regulatory compliance and corporate data security standards, SQL Server allows you to enable encryption at the columncell level or on the entire database level whereas hashing can be used for several purposes for example:
- Identifying incremental data or changed data - Hash values generated for an entire row (by concatenating values of all the columns of the row and then generating hash key on it) are useful for efficiently searching for differences between rows in tables and identifying if the rows have changed, in case there is no mechanism in place to identify incremental data on the source table.
- Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value.
- If you have a composite key on several lengthy columns, you can concatenate them and generate hash key on the concatenated value and then you can use this hash key as a joining key.
Encryption is bidirectional, which means data encrypted can be decrypted back to the original string if you have access to the correct decryption key, whereas hashing is unidirectional, which means hashed data cannot be reversed back to the original string.
Getting Started with Hashing

SQL Server has the HASHBYTES inbuilt function to hash the string of characters using different hashing algorithms. The supported algorithms are MD2, MD4, MD5, SHA, SHA1, or SHA2. The hashed data conforms to the algorithm standard in terms of storage size i.e. 128 bits (16 bytes) for MD2, MD4, and MD5; 160 bits (20 bytes) for SHA and SHA1; 256 bits (32 bytes) for SHA2_256, and 512 bits (64 bytes) for SHA2_512. SHA2_256 and SHA2_512 algorithms are available in SQL Server 2012 and later versions.
The stronger hash function you use, the more storage space it takes, and performance is slower but it provides a stronger hash value with minimal chance of hash collision (generating the same hashed output for two different input string of characters). Hence, it’s recommended to use hashing algorithms depending on your workload and data to hash by making it an appropriate trade-off.
The example below, demonstrates the use of the HASHBYTES function to do hashing using MD5 algorithm. As mentioned before, a slight change in the input string of characters produces a completely different hashed output and this is what you could see in the second column. The only difference between input for the first column and input for the second column is an extra space at the end of the input string in the second input string:

No matter how many times you do the hashing, the hashed output will remain same for the same set of input strings and same hashing algorithm:
Dec 01, 2016 putty ssh private + public key windows and linux with puttygen. Setting up SSH Keys on Windows using PuttyGen - Duration. Generate SSH Key Pairs to. 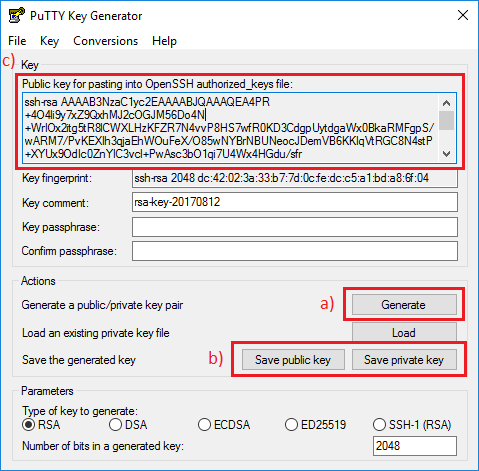 Jan 12, 2015 This tutorial shows you how to quickly and easily create a pair of SSH Keys using PuTTYgen, one tool in the open source PuTTY suite. You can find the written. It is possible to configure your Raspberry Pi to allow your computer to security access it without providing a password each time you try to connect to it. To do this you need to generate SSH keys. Apr 18, 2019 Hit enter to search. Online Help Keyboard Shortcuts Feed Builder What’s new.
Jan 12, 2015 This tutorial shows you how to quickly and easily create a pair of SSH Keys using PuTTYgen, one tool in the open source PuTTY suite. You can find the written. It is possible to configure your Raspberry Pi to allow your computer to security access it without providing a password each time you try to connect to it. To do this you need to generate SSH keys. Apr 18, 2019 Hit enter to search. Online Help Keyboard Shortcuts Feed Builder What’s new.
Sql Server Generate Hash
Based on the hashing algorithm you choose, your hashed output will change both in terms of value and size. For example, as demonstrated below, hashed output with MD5 algorithm produces a 16 bytes long value whereas SHA1 algorithm produces a 20 bytes long value:
You can use the HASHBYTES function in line with a SELECT statement when querying data from tables. It’s up to your requirement to hash a value from one column or multiple columns. For example, as you can see in the below query I am hashing combined values (by combining ProductNumber and Name) when querying data from the table.
Limitation of the HASHBYTES Function and how to Overcome It
The maximum length of input values to be hashed is limited to 8000 bytes - the HASHBYTES function gives an error, “String or binary data would be truncated” when the length of the input string is more than 8000 bytes. To overcome this limitation, I have written this user defined function, which overcomes the HASHBYTES function by splitting chunks of 8000 bytes of a large string, hashing each chunk individually and then combining each hash key together and finally generating a hash key for the concatenated hash keys. This workaround seems to be working fine in my case, but I would highly recommend you evaluate it in your scenario for your suitability and before putting it in use.
Once the user defined function is created as above, you can use it similar to the way shown below:
Conclusion
In this article, I discussed hashing in SQL Server and how to use it. I also talked about how hashing is different from encryption along with some use cases where hashing would be a good approach to take.
Resources
Sql Server Generate Hash Key In Photoshop
Sql Server Generate Hash Key Mac
| Latest Forum Threads | |||
| MS SQL Forum | |||
| Topic | By | Replies | Updated |
| SQL 2005: SSIS: Error using SQL Server credentials | poverty | 3 | August 17th, 07:43 AM |
| Need help changing table contents | nkawtg | 1 | August 17th, 03:02 AM |
| SQL Server Memory confifuration | bhosalenarayan | 2 | August 14th, 05:33 AM |
| SQL Server – Primary Key and a Unique Key | katty.jonh | 2 | July 25th, 10:36 AM |